Change firewall rules
This section describes the configuration settings relating to the firewall.
For configuration settings relating to the Deployment components, see Internal Corporate Network Rules for firewall rules required for the internal corporate network. See External / Internal rules for which ports to open and also see Additional firewall rules.
Windows device support requirements
Autodiscovery allows Windows devices to seamlessly register with Core. The following set up is required for using autodiscovery with Windows devices:
-
Create DNS A record to point to Core
-
Obtain a TLS/SSL SAN certificate from a trusted Certificate Authority (CA)
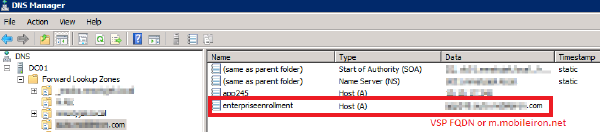
Create DNS A record
Create a DNS A record that refers DNS requests for enterpriseenrollment.YourCompanyDomainName.com to the Core IP address.
YourCompanyDomainName must match the domain of the email addresses used for registering with Core.
Figure 1. Enterprise enrollment
Obtain a TLS/SSL SAN certificate
For Windows devices, a Subject Alternative Name (SAN) TLS/SSL certificate from a trusted Certificate Authority (CA), such as Verisign or GoDaddy, is required. If you use a self-signed (localCA) certificate, device enrollment will fail.
-
The TLS/SSL certificate provides trusted and secured connection without certificate warnings.
-
A SAN certificate, also known as a multi-domain certificate or a unified communication certificate, is valid for two or more hosts. The SAN certificate must cover the Core hostname and enterprise enrollment.YourCompany-Domain name.com.
Connecting to the Windows store
You can set up recommended apps that device users can download from the Apps@Work app. For Windows devices, your firewall must allow connections to the following hosts:
|
Purpose |
Host connection |
|---|---|
| Windows 10 app store search | https://storeedgefd.dsx.mp.microsoft.com |
| Windows 10 VPN for Cisco AnyConnect | https://www.windowsphone.com |
| Windows Phone 8 App store detail URL | http://marketplaceedgeservice.windowsphone.com |
| Windows Phone 8 app store icon URL | http://cdn.marketplaceimages.windowsphone.com |
AppConfig Community Repository outbound firewall port setting
Core requires outbound firewall access on TCP port 443 to https://appconfig.cdn.mobileiron.com/com.example.OneTouchConfiguration/current/appconfig.xml for the Managed App Configuration UI to render properly.
|
Purpose |
Host connection |
|---|---|
|
Android Help@Work |
|
| Appthority | https://api.appthority.com/applications/bulk_query |
|
Azure active directory |
https://graph.windows.net/%s/devices/deviceId_%s?api-version=1.6 |
|
BlueCoat |
|
| Business Store Portal (BSP) | https://onestore.microsoft.com |
|
Business Store Portal (BSP) |
|
| For the Find My Phone mapping and other options | https://api.mqcdn.com/sdk/mapquest-js/v1.0.0/mapquest.css |
|
GlobalSign |
|
|
iOS Managed AppConfig community |
|
|
Microsoft Graph |
https://login.microsoftonline.com/{tenant_id}/oauth2/authorize |
|
Samsung E-FOTA |
|
| SymantecManagedPKI | pki-ws.symauth.com |
|
Windows device attestation |
https://has.spserv.microsoft.com/HealthAttestation/ValidateHealthCertificate/v1 |